OPERATIONS OF ENDPOINT SECURITY MANAGEMENT
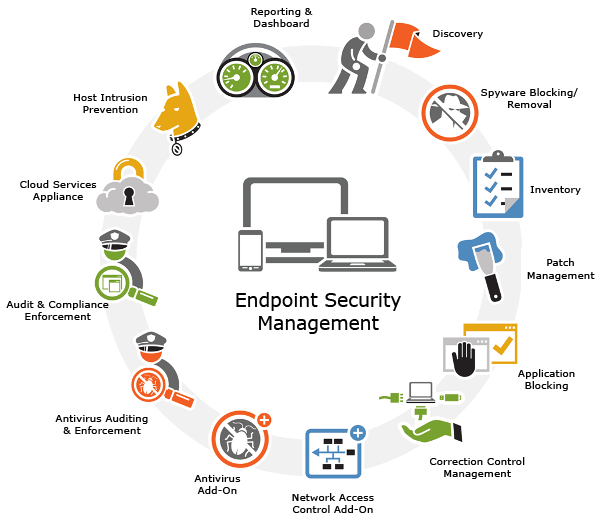
Endpoint Security Management refers to the protocols for restricting network access from cellular phones or computing device. Each device represents an endpoint that must be monitored or needs appropriate authorization or administrative controls. In general, endpoint security management can be a minor part of the comprehensive IT security. Several employees use personal devices for work. […]
ENHANCING SECURITY WITH SECURE INTERNET GATEWAY AND DNS CONTROL

In the current digital climate, it’s imperative that we secure our online systems. Using DNS operation in confluence with a Secure Internet Gateway (SIG) is one practical action to boost security. A Secure Internet Gateway (SIG) is one type of network security that protects businesses from colorful pitfalls and provides Secure Internet Access. As […]
NEXT-GEN VS TRADITIONAL ENDPOINT PROTECTION: A COMPARATIVE ANALYSIS

Cybersecurity threats are changing at an alarming rate in the modern digital ecosystem, necessitating ongoing defensive strategy adaptation on the part of enterprises. Endpoint protection, which defends individual devices like laptops and smartphones, is an essential part of an all-encompassing cybersecurity system. However, the initiation of next-generation endpoint security products has spurred discussion over their […]
Delving Into The Dark Side Of The Tech Revolution Hackers

The term “tech revolution” describes technology advancement with regards to time. New additions have paved way for changes in living standards, especially in homes. Moreover, technology has transformed business, entertainment, communication, and other facets of life drastically. Join a community of skilled hackers. Elevate your cybersecurity game with expert guidance and resources. It has had […]
THE INTRUSION OF RANSOMWARE INTO YOUR PC: HOW DOES IT HAPPEN?

Ransomware is a malicious program that cybercriminals use to decrypt your security protocols and gain access to files and information. After overhauling the system, they inquire for a ransom in exchange of the compromised security. Malware is a specific term for an unwanted software that enables access to a device. Ransomware is a subset of […]
TAILORED ENDPOINT SECURITY SOLUTIONS FOR ENTERPRISE PROTECTION

What’s better than having a robust security system for your digital transactions and data? To evolve your firm to new heights, reinforcing endpoints (mobile phones, laptops, workstations, etc.) is essential. Traditional antiviruses are no longer a plausible solution: The best remedy is a security system that quarantines, reports, or eliminate cyber threats instantly. After all, […]
STRATEGIES FOR DEALING EFFECTIVELY WITH A RANSOMWARE THREAT

Do you know about the BlackCat Ransomware Group that launched a malicious attack inflicting 233 German gas stations in 2022, causing the oil company, Shell, to redirect supplies to various storage depots? According to the German Intelligence Services, two software applications, namely Microsoft Exchange and Zoho Adshelf Service Plus 1 were compromised. Protect your data […]
EXPLORING ANTI MALWARE AND ITS ROLE

The dangers of cyber threats are increasing rapidly in the modern digital world. Malicious software, or malware, is one of the most common and destructive applications against SMEs, corporations, and MNCs. Defend your devices against cyber threats with powerful anti malware protection. Its goal is to intrude, interfere with, or obtain illegal access to user […]
Analyzing Ransomware Attack Methods On Computers

In the modern technological era, hackers are evolving at a rapid pace, embezzling data for ransom, or extorting money with a ransomware attack. They focus on blackmailing firms into submission. Moreover, they expect higher returns. Hackers target local governments, educational institutions, technological firms, healthcare facilities, manufacturing firms, financial services, and media organizations. All businesses and […]

