Top 10 Cyber Security Attacks Post 2017: A Comprehensive Analysis

In the technological era, firms and businesses have accepted new developments with open hands. Their working mechanism and processes have been reinforced with cybersecurity protocols, making headway from simple antiviruses to XDR (Extended Detection and Response) services. Protect your digital assets from cyber security attacks with robust solutions and proactive measures. However, with rising security […]
Proactive Measures To Prevent Ransomware Incidents

Data protection and safety has become a prime concern for the digital world. Companies and industries are being targeted by global hackers who malign security protocols and encrypt sensitive information for malicious motives. Some demand huge sums of money while others want recognition on the main stage. Safeguard your data and systems with effective ransomware […]
Insights Into Ransom Virus Attacks And Their Impact

Have you ever felt chained in your life? In a place where you cannot motion around freely? Well, similar is the case with a user who is under duress from a ransomware attacker who threatens to disseminate sensitive information to the dark web or online. Or, perhaps, damage his trustworthy clients with other demeaning tactics. […]
Embracing The Cloud The Future Of Endpoint Security

As for the latest developments in the cyber world, endpoint security has become a mandatory aspect for safeguarding organizations against threats of different kinds. With the proliferation of endpoints due to cloud adoption, IoT expansion, and remote work, the attack parameters have broadened, requiring inventive approaches from threat-evading systems. The future of endpoint security is […]
Understanding The Rapid Spread Of Ransomware On Networks

Ever witnessed a ransom taking place? All the perpetrators do is kidnap someone and ask for a hefty sum of money. Digital ransom attacks are also managed similarly: The embezzlers hijack sensitive information from PCs, laptops, or cloud computing systems and threaten the owners for ransom. If not paid in due time, they would spread […]
Deciphering The Menace Of Computer Ransomware Attacks

With a growing digital landscape, unwanted intrusions (ransomware in particular) are emerging as a potent threat, affecting entrepreneurs, businesses, and even nations. Ransomware is a kind of malware that encrypts information on a system, such as a PC or laptop, rendering it inaccessible until the ransom is delivered to the perpetrators. Protect your data from […]
EXPLORING ANTI MALWARE AND ITS ROLE

The dangers of cyber threats are increasing rapidly in the modern digital world. Malicious software, or malware, is one of the most common and destructive applications against SMEs, corporations, and MNCs. Defend your devices against cyber threats with powerful anti malware protection. Its goal is to intrude, interfere with, or obtain illegal access to user […]
Analyzing Ransomware Attack Methods On Computers

In the modern technological era, hackers are evolving at a rapid pace, embezzling data for ransom, or extorting money with a ransomware attack. They focus on blackmailing firms into submission. Moreover, they expect higher returns. Hackers target local governments, educational institutions, technological firms, healthcare facilities, manufacturing firms, financial services, and media organizations. All businesses and […]
PRIMARY PROBLEMS IN ENTERPRISE ENDPOINT SECURITY IN PRESENT TIMES
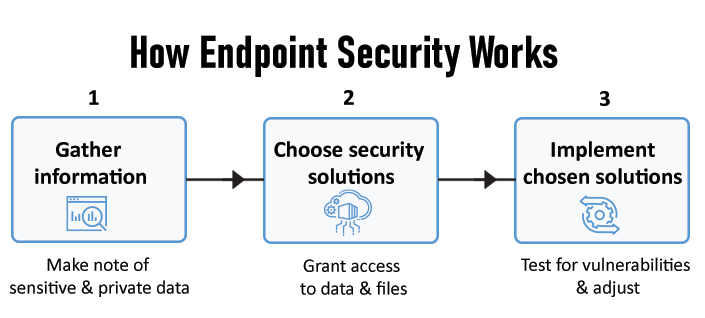
“Threat actors never sleep…. neither can your security.” These reverberating lines by Jonathan Jackson (Director, Sales Engineering, APJ) reflect the significance of a multi-layered security system for organizations, enterprises, and startups, predominantly to safeguard resources (assets and financials) and ensure optimal growth. Fortify your enterprise with advanced endpoint security. Novasecuris ensures robust protection, safeguarding endpoints […]
WHY IS MDR CYBERSECURITY SERVICE SIGNIFICANT FOR BUSINESSES?
With advancements in online security systems, businesses or corporations want to fortify their assets and information with the best solutions. Most of them are willing to pay a hefty price for the latest technology, provided it deters or culminates the looming cyber threat: EDR (Endpoint Detection and Response) is a cybersecurity solution that monitors and […]

