THE INTRUSION OF RANSOMWARE INTO YOUR PC: HOW DOES IT HAPPEN?

Ransomware is a malicious program that cybercriminals use to decrypt your security protocols and gain access to files and information. After overhauling the system, they inquire for a ransom in exchange of the compromised security. Malware is a specific term for an unwanted software that enables access to a device. Ransomware is a subset of […]
Delving Into The Dark Side Of The Tech Revolution Hackers

The term “tech revolution” describes technology advancement with regards to time. New additions have paved way for changes in living standards, especially in homes. Moreover, technology has transformed business, entertainment, communication, and other facets of life drastically. Join a community of skilled hackers. Elevate your cybersecurity game with expert guidance and resources. It has had […]
NEXT-GEN VS TRADITIONAL ENDPOINT PROTECTION: A COMPARATIVE ANALYSIS

Cybersecurity threats are changing at an alarming rate in the modern digital ecosystem, necessitating ongoing defensive strategy adaptation on the part of enterprises. Endpoint protection, which defends individual devices like laptops and smartphones, is an essential part of an all-encompassing cybersecurity system. However, the initiation of next-generation endpoint security products has spurred discussion over their […]
ENHANCING SECURITY WITH SECURE INTERNET GATEWAY AND DNS CONTROL

In the current digital climate, it’s imperative that we secure our online systems. Using DNS operation in confluence with a Secure Internet Gateway (SIG) is one practical action to boost security. A Secure Internet Gateway (SIG) is one type of network security that protects businesses from colorful pitfalls and provides Secure Internet Access. As […]
OPERATIONS OF ENDPOINT SECURITY MANAGEMENT
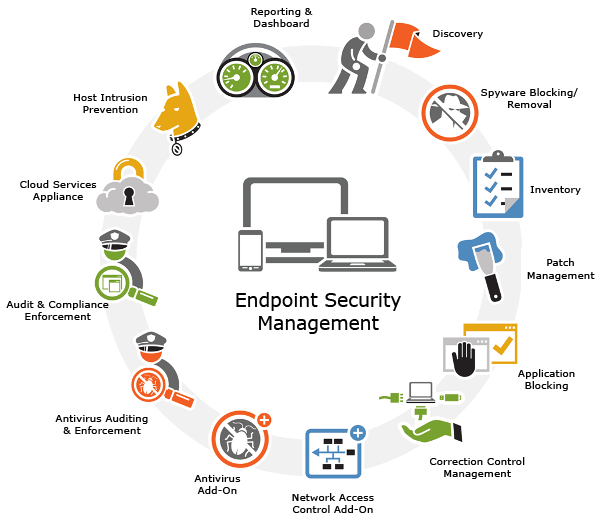
Endpoint Security Management refers to the protocols for restricting network access from cellular phones or computing device. Each device represents an endpoint that must be monitored or needs appropriate authorization or administrative controls. In general, endpoint security management can be a minor part of the comprehensive IT security. Several employees use personal devices for work. […]
Understanding Managed Detection and Response (MDR)
Also known as Managed EDR, Managed XDR, and MXDR, Managed Detection and Response or MDR is a cybersecurity offering that requires a professional unit to track and monitor endpoints, networks, and cloud environments. A good MDR service provider alleviates the expense and effort required by a firm to derive value from an EDR solution. Moreover, […]
Why Should You Hire A Cyber Security Services Company?

According to an eminent US statesman, “Cyber security is a shared responsibility, and it boils down to this: In Cybersecurity, the more systems we secure, the more secure we all are.” The field of cybersecurity is new and expanding; it is dependent on automated systems built to diffuse threats perpetrated by hackers and organized crime […]
WHY IS MDR CYBERSECURITY SERVICE SIGNIFICANT FOR BUSINESSES?
With advancements in online security systems, businesses or corporations want to fortify their assets and information with the best solutions. Most of them are willing to pay a hefty price for the latest technology, provided it deters or culminates the looming cyber threat: EDR (Endpoint Detection and Response) is a cybersecurity solution that monitors and […]
PRIMARY PROBLEMS IN ENTERPRISE ENDPOINT SECURITY IN PRESENT TIMES
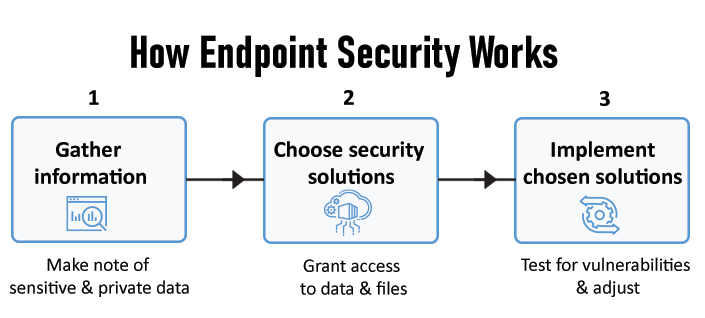
“Threat actors never sleep…. neither can your security.” These reverberating lines by Jonathan Jackson (Director, Sales Engineering, APJ) reflect the significance of a multi-layered security system for organizations, enterprises, and startups, predominantly to safeguard resources (assets and financials) and ensure optimal growth. Fortify your enterprise with advanced endpoint security. Novasecuris ensures robust protection, safeguarding endpoints […]

