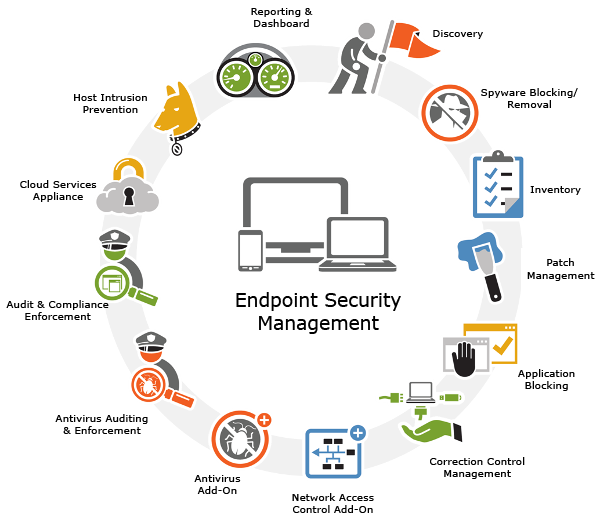
Endpoint Security Management refers to the protocols for restricting network access from cellular phones or computing device. Each device represents an endpoint that must be monitored or needs appropriate authorization or administrative controls. In general, endpoint security management can be a minor part of the comprehensive IT security.
Several employees use personal devices for work. A large potential of data can be hacked or embezzled, based on the security strength of the electronic gadget accessing a computer network. Enterprise vendors have packed a multitude of features into programs to help firms improve their security process across the board. This may include protecting hardware assets and network.
Endpoint security management system can be build in-house, delivered as individual software applications, or refer as a web-delivered cloud feature within a package of service.
Table of Contents
ToggleEndpoint Security: What Is It?
Endpoint security has become crucial in IT security due to the rise in cyber threats and data breaches. This comprehensive tutorial is for you if you’ve ever wondered, what is Endpoint Security Management? or how does Endpoint Protection work?
Understanding endpoint security’s concept, significance, and operating mechanism is important because of the various types of endpoint security. If there is a lapse in the security system, malicious cyber-attacks can breach and compromise digital devices or entire networks.
A Single Approach to Protecting Several Endpoints
Enterprises must establish “security rules or policies” that guarantee employees have access to business data without leaving any gaps in the network that could allow hackers to exploit it. Endpoint Security Management is the policy-based approach to network security that requires endpoint devices to meet all requirements of the network’s resources.
How Does Endpoint Security Management Operate
Endpoint Security Management solutions operate using a client/server architecture in which security software is hosted on the server and deployed on the clients’ network devices. The server verifies the devices after a client connects to the network. The system reviews the user credentials and inspects the devices to follow the company’s policy before granting access.
Several actions are taken to guarantee ongoing protection:
· Installing the Endpoint Protection Software
All network-connected devices, including servers, workstations, mobile phones, and IoT (Internet of Things), remain in the initial stage of the installation and integration process of endpoint security protection. Depending on the vendor, the software can connect with existing security infrastructure to build a unified defense system.
· Policy Formulation and Implementation
Policies are created for security purposes: On the network, these guidelines specify the types of actions recommended for normal functioning. Data transit, application usage, and access permissions are some attributes that policies can regulate. All endpoint devices must abide by these policies.
· Threat Detection
Endpoint security software scans the network for potential threats. It depends on advanced technologies, such as machine learning and behavioral analysis to identify abnormal behavior or malevolent trends. The system notifies the administrators if any such activity is present.
· Threat Response
The endpoint security process is an automated one; it isolates the device from the network and restricts it from inflicting harm. The modifications (security changes) depend on the system configuration and the type of attack.
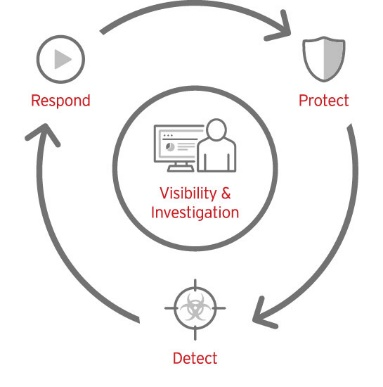
· System Update and Maintenance
As technology is advancing continuously, the endpoint protection systems must be updated concurrently. Regular updates ensure that the system possesses modern defense mechanisms against incoming threats. Moreover, system health checks are also mandatory for smooth operations.
· Analysis and Reporting
The endpoint security system garners data on system operations and malicious intrusions. The information shown in reports gives administrators a clear picture of the endpoint security status and potential vulnerabilities. This insight allows for better decision-making and proactive threat management.
· Learning and Adaptation
Regarding constant learning and changes, advanced endpoint protection systems employ AI and machine learning to enhance their threat detection and response capabilities over time. Endpoint security adapts to the changing threat landscape and restricts threats, turning into a proactive rather than a reactive defense.
Which Components make up Endpoint Security?
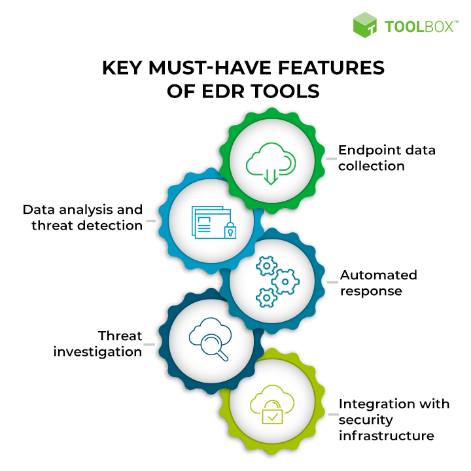
Endpoint security technologies are a combination of security tools like firewalls, host-based intrusion detection/prevention systems, vulnerability assessment tools, and antimalware software.
Benefits of Endpoint Security
Following are some potent advantages of endpoint security:
· Endpoint Protection
Due to digital transformations, employees can work remotely and protect endpoints to prevent breaches.
· Identity Protection
Only authorized users have access to sensitive information. Identity protection safeguards the confidential information of employees and other stakeholders. It is a significant aspect of endpoint security.
· Identification and Threat Mitigation
A high number of attackers attempt to penetrate organizations through cyberattacks, identifying possible risks to expedite the remediation process and ensure data security.
Is Endpoint Security Required for Every Business?
It depends on how businesses handle their data. Naturally, the demand for endpoint security would increase with the level of permission. With a variety of portable device types, endpoint security is essential for all businesses, regardless of size.
Frequently Asked Questions
Q.1. What are three main types of endpoint security?
Ans. The three types of endpoint security systems are:
- Endpoint Protection Platform (EPP)
- Endpoint Detection and Response (EDR)
- Extended Detection and Response (XDR)
Q.2. What is an endpoint in API?
Ans. An API endpoint is a site where API obtains requests about a certain source on its server. In general, it is a URL (Uniform Resource Allocator) that renders the position of the server.
Q.3. What is SIEM used for?
Ans. SIEM (Security Information and Event Management) assists firms to identify, evaluate, and respond to security threats before any intrusions take place. It offers the following functions:
- Log Management
- Event Correlation
- Incident Monitoring and Response